The cybersecurity industry eagerly awaits the release of the Verizon Data Breach Investigations Report (DBIR) each year. On June 6, 2023, the DBIR delivered its observations from the last year, with plenty of its infamous snarky humor to accompany the otherwise-serious subject of cyber incidents and breaches.
For anyone reading the DBIR for the first time, it might strike you as overwhelming to see, in print, all the things threatening organizations and individuals. The authors of the report analyzed 16,312 security incidents, 5,199 of which were cited as confirmed breaches. These numbers in a silo are impressive, but you have to remember that the data for the DBIR are limited to only what’s known and/or reported via public information (including the VERIS Community Database) and sponsors’ contributions. In other words, while the DBIR team is doing phenomenal work to aggregate and analyze as many sources as possible, information is missing. Why? Because companies don’t always like to share when they experience a cyber incident…or even a breach. The result: blind spots in data.
The fact that so many data sources are used for the DBIR means that the analysis is, indeed, trustworthy and indicative of overall industry trends. But also keep in mind that the scale of the cyber problem is bigger than what can be collected and presented in any one report.
What are attackers up to?
Who
The DBIR has changed a lot over the 16 years it has been in existence so it’s hard to do an apples-to-apples comparison on the Summary of Findings.
External actors
Looking back just one year, however, reveals that external threat actors continue to be the leading source of trouble when it comes to the “who” behind the “what.”
Without question, external threat actors overwhelmingly perpetrate incidents and breaches. Compared to the 2022 DBIR, external actors’ actions contributed only 3% more than last year — a negligible change. However, the gaps to the next threat actor group, internal actors, is so wide that it barely matters what the one-year change was. Year-over-year, external actors continue to be the most significant threat actor group causing cybersecurity events, a fact that is not likely to change anytime soon, and a data point that should play into organizations’ cyber defense strategies.
Organized Criminals
Nation-state threat actors get a lot of press, but when it comes down to which external threat actors are assailing our organizations, it’s significantly organized crime groups.
Just like any other business, organized cybercrime groups are composed of workers with different roles and responsibilities, different skill sets — including marketing, finance, operations — and even performance goals. Members of these groups are motivated and well funded, just like nation-state actors. The main difference is that they’re generally not after state secrets. In other words, private sector, they’re coming for you.
How
Credentials
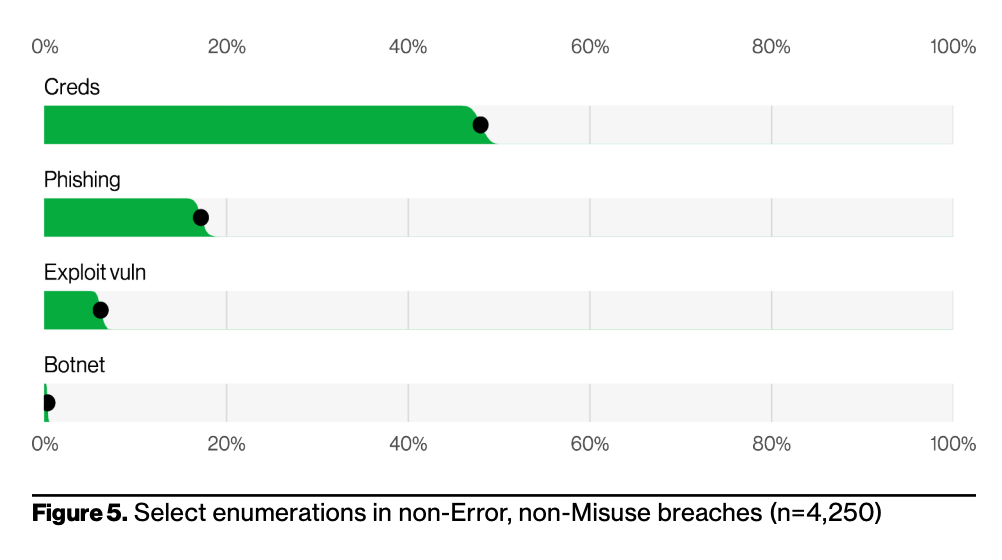
We see similar trends with the “how,” i.e., the ways in which threat actors compromise an organization.
Credential theft dominates threat actors’ tactics when it comes to successful cyber compromise. Because it works. This trend is worrisome. It should not be news to any cybersecurity practitioner that credentials are a leading avenue to incidents and breaches. The industry has been talking about hardening access controls for years, and multi-factor authentication (MFA) is one very effective way to ensure a reduction in compromised accounts, which lead to greater system exploitation. While some organizations might still find it challenging to convince executive teams to approve the mandate of MFA, passwordless authentication, password vaults, or other enhanced access mechanisms, the data should speak for itself. It’s well past time to make it harder for cyber criminals to use valid credentials to gain system access.
Social engineering
Tending to the credential problem is especially important considering that social engineering also continues to be a leading tactic for successful exploitation. Everyone knows (or should know) by now that a Nigerian Prince is not going to send millions of dollars if the user clicks on a link or fills out a form. But while phishing continues to work (despite the absurdity of promised free money from a stranger), threat actors are turning to pretexting more often than in the past. Why? Because pretexting, unlike phishing, focuses on trust building and impersonation that may be hard for users to spot, if done correctly.
This tactic is so effective that the DBIR reports a 50% increase in incidents caused by business email compromise (BEC), a form of pretexting, over 2022.
The key to a successful pretext attack is conviction — the attacker creates a plausible story or scenario which the victim is likely to believe. The attacker then uses the small amount of trust built on the lie to persuade the victim into unintentional malfeasance. Unfortunately, there are fewer security controls, when compared to other types of attacks, that can be deployed to prevent pretexting; the most effective method of prevention is end user awareness and education. However, while pretexting is likely to continue as an attack method, security teams should be investing heavily into secondary security controls that prevent the attack from propagating further after the initial entry point.
Ransomware
A cybersecurity report would not be complete without mention of ransomware and its prevalence. According to the DBIR, “Ransomware continues its reign as one of the top Action types present in breaches.” Notably, the number of reported ransomware attacks didn’t increase this year, but the hockey stick growth starting in 2021 makes it one of the predominant action varieties.
Ransomware is a tough nut to crack from a defense perspective, but organizations should up-level their endpoint (and especially email) controls, patch whenever possible, practice strong security hygiene, and (of course) maintain backups. So simple, right? <sarcasm>
What
Servers, people, and user devices
People and users often get all the blame when an organization is attacked: “People are our weakest link.” “ Sally opened an attachment she shouldn’t have.” “Fred’s accounts were over-permissioned and his credentials were stolen.” But if you’re going by the data, servers are the most popular attack target, by far.
Notably, the top categories of affected assets in breaches hasn’t changed appreciably in the last several years. What, exactly, is a server according to the DBIR’s author’s? Their definition is:
Server (srv): a device that performs functions of some sort supporting the organization, commonly without end-user interaction. Where all the web applications, mail services, file servers and all that magical layer of information is generated.
Why is this asset classification important? Because it gives defenders a place to start when deciding the order of controls importance. While there is no one-size-fits-all when it comes to cybersecurity strategy and tactics, it’s a good idea to focus first efforts on the assets known to be coveted by attackers. Once these assets are identified (including those in cloud environments), security teams can deploy zero trust-based controls for access, segment networks and data, tune firewalls, apply advanced encryption, keep systems updated and patched, check configurations, and log and monitor server events continuously.
Lots more to read
The DBIR is the War and Peace of cybersecurity, so there’s plenty more juicy data in there for every practitioner. Just like the practice of cybersecurity itself, check out the original resource and chunk it off in consumable pieces. While the data, in and of itself, is interesting, it’s of most use when the data is used to inform your security program.